The dangers of encryption "hidden dangers", improve self-protection awareness! (Chrome protection tutorial included)
Yesterday, basically everyone was talking about the fact that a certain user’s funds were stolen from the exchange, resulting in a loss of 1 million US dollars. You can look up the various reasons yourself, so I will not go into details.
With the continuous development of the encryption era, science and technology are advancing, blockchain technology is advancing, and hacker technology is also advancing. Various endless hacker attacks have caused losses to many people. Although it did not happen to us this time, it has also aroused our vigilance. Under the hidden dangers of encryption, it is very important to improve our self-protection awareness.
The main reason for the theft was Chrome's plug-in. As the most widely used browser in the encryption field, Chrome has also been used as a tool for "making money" by many criminals. Therefore, to improve your self-protection awareness, you must first learn how to use Chrome!
In the evening, I looked up some information and sorted out some effective ways to improve the security of Chrome. Although it is better than nothing, I hope it will be useful to everyone.
First, a blogger suggested self-checking Chrome plug-ins, especially checking the permissions of existing plug-ins.
As for Chrome plug-ins, everyone uses them for convenience. However, now there are plug-in problems, everyone is worried. It is unrealistic to delete all the plug-ins, so we can only check ourselves, especially the plug-in permissions.
Click the three dots in the upper right corner of Chrome and select Extensions
Select the plug-in you want to self-check and click Details.
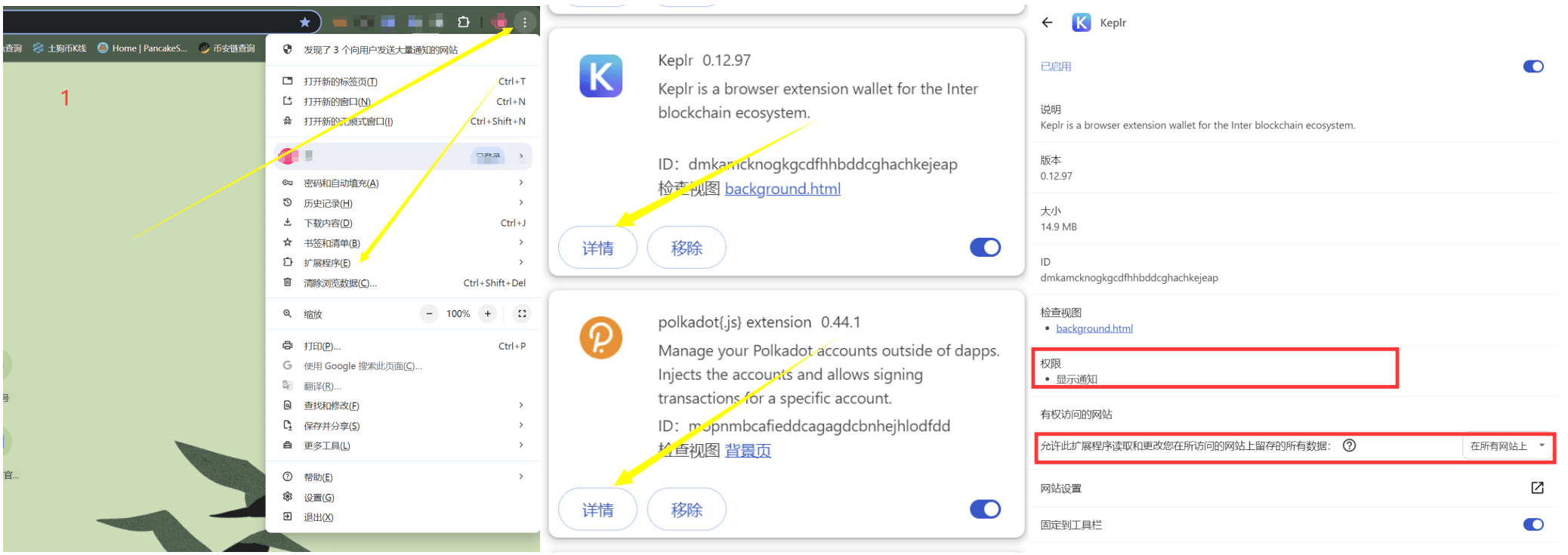
Check the permissions column of the plug-in. Please note that there may be two different descriptions here, so pay attention.
"Allow this extension to read and change all your data stored on sites you visit"
"Read and change all your data on all sites"
Most people ignore the descriptions here, and are the easiest to fall into.
"Allow this extension to read and change all your data stored on sites you visit"
This permission usually means that the extension can only access data from the website the user is currently visiting. The access permissions are dynamic and change as the user browses different websites.
This permission is limited and only works on websites that users actually visit, so the privacy risk is relatively low. At the same time, the extension cannot perform any operations on unvisited websites in the background. This prevents you from being maliciously attacked or tampered with when you are not paying attention.
In addition, the description is usually followed by options, as shown in the figure, and the permission content can be adjusted according to your choice.
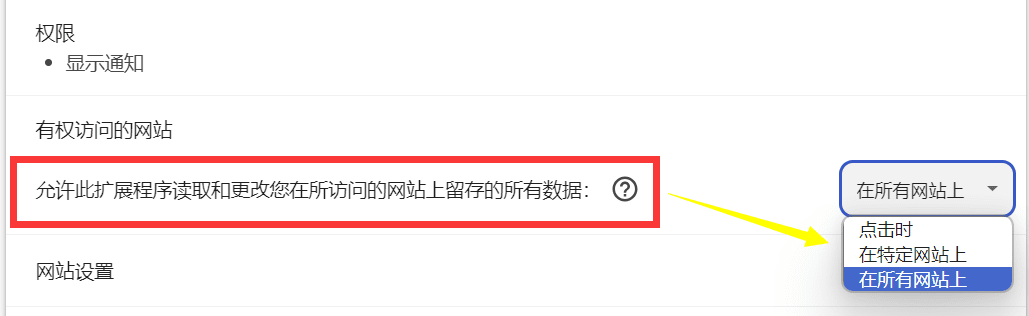
"Read and change all your data on all sites"
This permission is more extensive and allows the extension to access data for all websites in your browser.
Extensions can run in the background and access data for all websites, whether or not you're currently visiting a specific website.
This permission is very broad and poses a high privacy risk because the extension can access all the data in your browser.
If the extension is used maliciously, it could leak sensitive information such as passwords, banking details, and browsing history.
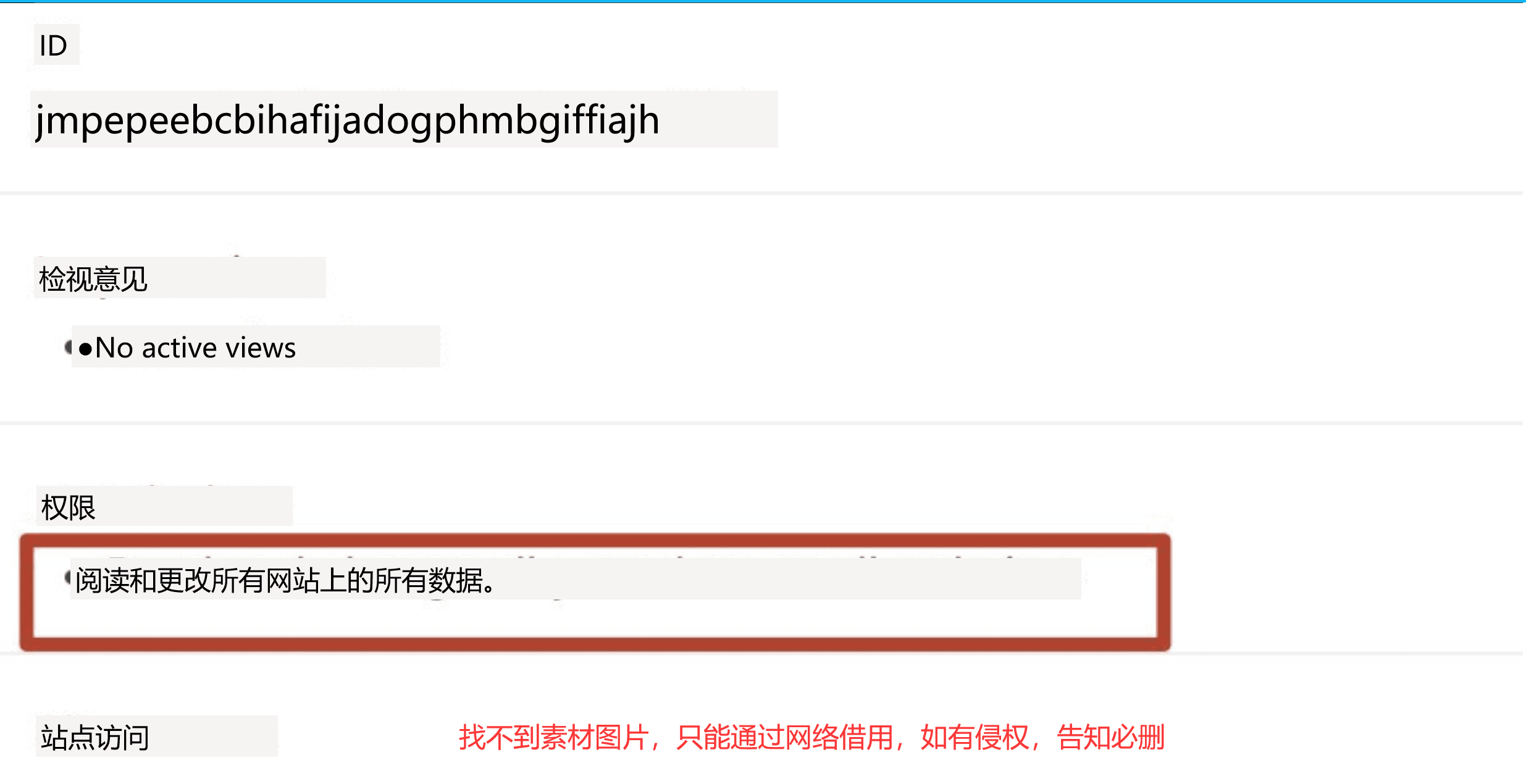
Through understanding, we can understand that our self-check mainly excludes the permissions described in the second type. At the same time, if we find that there is no second type, then we can also appropriately set permissions for the first type to improve protection.
Second, how to avoid risks?
1. Choose trusted extensions, that is, plug-ins that are officially recognized or developed by well-known developers (with credibility).
2. Check permission requests and permission requirements regularly. At the same time, adjust the public permissions of individual plug-ins that you do not trust, downgrade them, or delegate them.
3. Read user reviews and ratings. When downloading plug-ins, pay attention to user ratings and comments. If you find that the comments are incorrect, download it immediately and carefully, or download it separately.
4. Regularly self-check. Just like using a cold wallet, you should regularly self-check your permissions.
5. Use security tools. This is a controversial topic, so everyone can express their opinions. I personally do not make any recommendations.
6. Stay vigilant. When browsing or using the software in daily life, be alert to pop-up windows from your browser or anti-virus software. If you don’t understand something, you can ask GPT immediately. After all, AI is very convenient nowadays, and we need to use the tools reasonably to protect ourselves.
Third, enable Chrome security settings and increase the protection level.
This is a problem that many people tend to overlook. Chrome is a good tool, but you have to learn how to use it. Chrome itself has self-protection, but many people don't know how to set it up, so the low level allows criminals to take advantage of the opportunity.
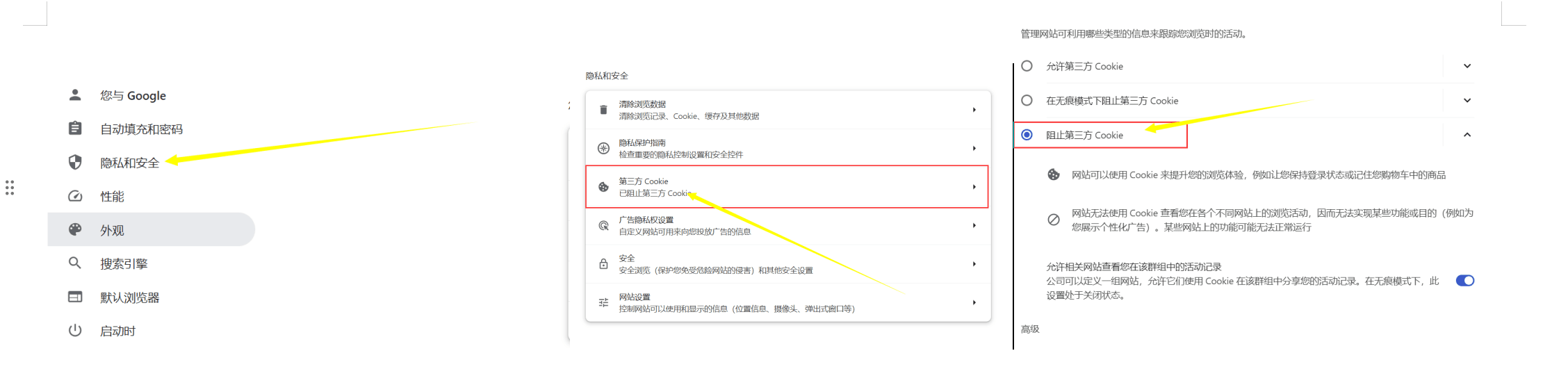
1. Prevent third-party tracking
Enable Do Not Track requests
Open Google Chrome.
Tap on the three dots icon (More options) at the top right corner.
In the drop-down menu, select Settings.
On the left side of the settings page, click Privacy and Security.
Click on Third-party "Cookies"
Click to block third-party cookies.
If you don’t know how, look at the picture.
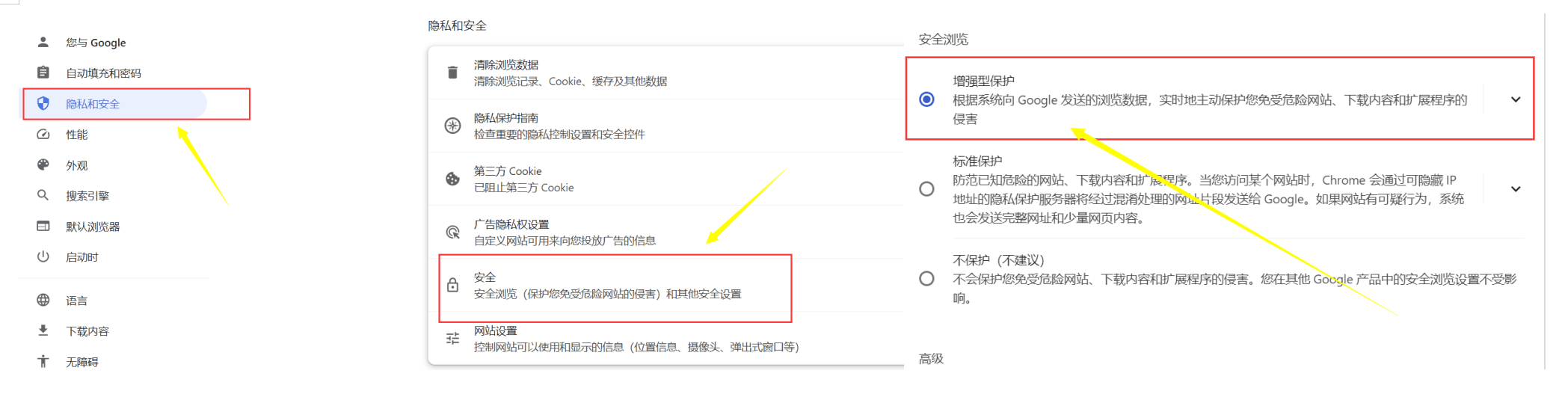
2. Enable safe browsing
Enable Safe Browsing protection
Still on the Privacy and Security page.
Click Security.
In the Safe Browsing section, select Enhanced protection or Standard protection.
Enhanced Protection: Provides a higher level of protection to proactively prevent and alert you to potentially dangerous events.
Standard protection: Provides basic protection and alerts you to potential dangerous events
If you have bad usage habits or browse dangerous websites, it is recommended to choose enhanced protection mode.
If you don’t know how, look at the picture.
3. Other privacy and security settings
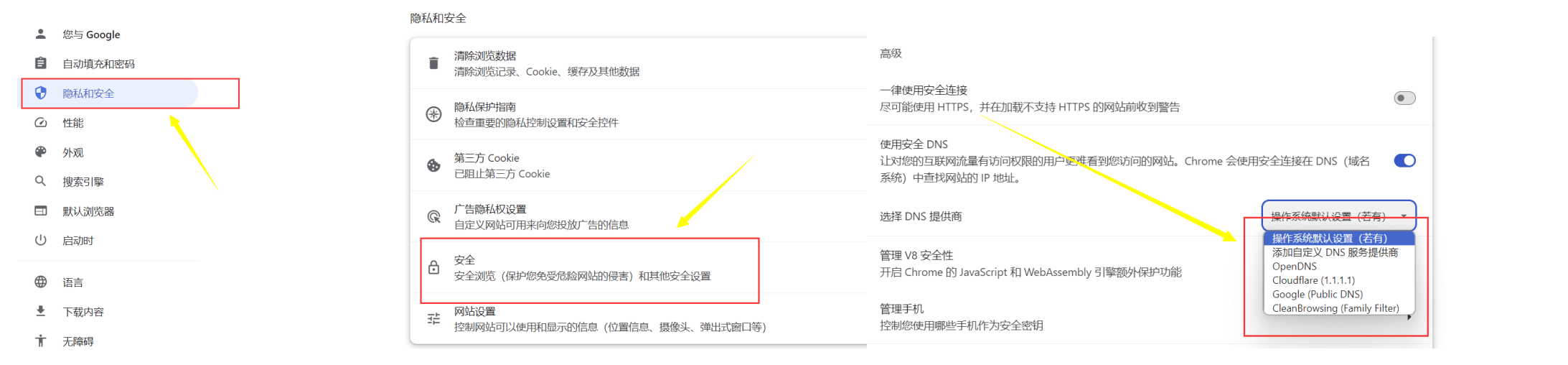
Enable sandbox protection
On the Privacy and Security page.
Click Security.
Scroll down, find “Use secure DNS”, and turn it on. Select a public DNS provider like Google (8.8.8.8) or Cloudflare (1.1.1.1).
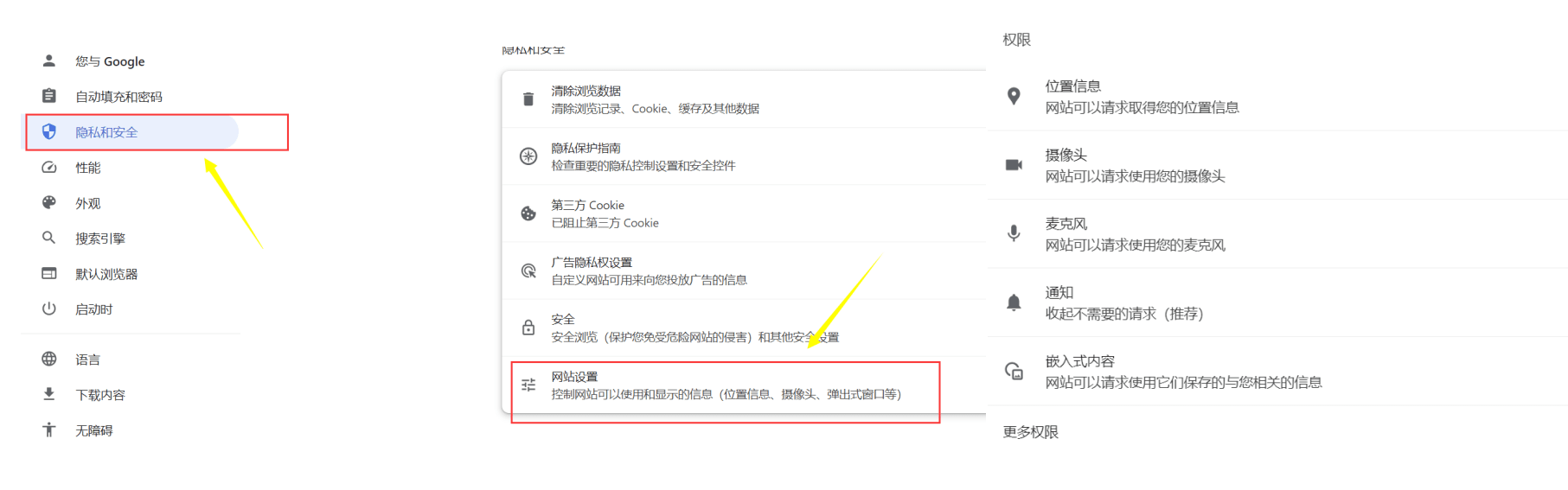
Check website permissions
On the Privacy and Security page.
Click Site Settings.
Here you can manage permissions for websites, including location, camera, microphone, notifications, JavaScript, etc. It is recommended to check regularly and limit unnecessary website permissions.
(There is not enough space, so the pictures are placed in the comment area)
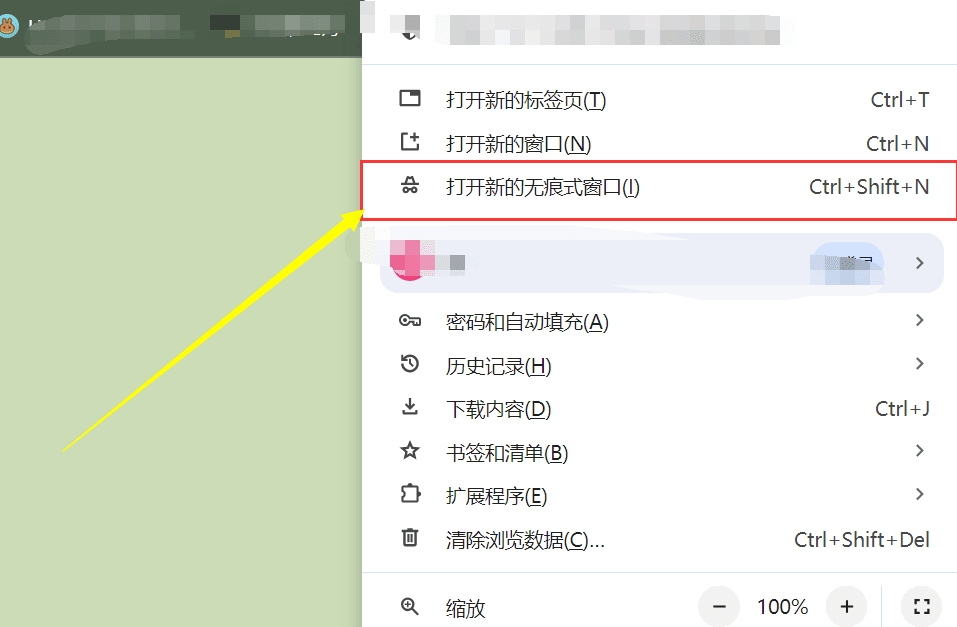
4. Browse in Incognito Mode
Incognito mode can be used when you don't want your browsing history, cookies, and other website data to be saved.
Tap on the three dots icon (More options) at the top right corner.
Select Private browsing.
Pay special attention to setting relevant cookie settings when setting up protection. The victims of this incident had their cookies stolen because their cookies were hacked.
What are cookies?
Cookies are small data files stored by websites in a user's browser. They can save a user's preferences, login information, and other website-specific information to provide a more personalized experience the next time the user visits.
To put it bluntly, if we get your personal cookie, we can basically get your usage data, including your account and password.
What are third-party cookies?
First-party cookies: Cookies that are set and read by websites that users visit directly. For example, when you visit a news website, the cookies set by this website are first-party cookies.
Third-party cookies: Cookies that are set and read by domains other than the website that the user is visiting (third parties). For example, when you visit a news website and this website contains advertisements from advertising networks, the cookies set by these advertising networks are third-party cookies.
So after reading this, everyone understands how much damage will be caused if there are problems with third-party cookies or if they are malicious cookies. So I hope everyone will check themselves and improve their security level.
The above is what I have found and transferred to you to the best of my ability. I basically use these myself, and I hope they are of some help to you. Of course, if you are able to use other methods, you will have to consider it.
#加密安全 #网络安全防护
