Key Points
In the Web3 world, unlimited authorizations create vulnerabilities that hackers can exploit through smart contract vulnerabilities or social engineering attacks.
Regularly check and revoke unnecessary authorizations to eliminate unauthorized asset access.
Use tools like Binance Web3 Wallet to protect your funds and stay alert to Web3 security risks.
In the decentralized finance space, what are the consequences of neglecting a single authorization? While smart contracts can simplify transactions, interacting with them also brings specific security risks, especially when users authorize third parties to access and manage their funds without limitations. In a previous blog, we discussed the risks of smart contract authorization and external accounts (EOA). This article will delve into other authorization risks and how to protect assets from threats, focusing on Ethereum Virtual Machine (EVM) chains.
Introduction to EVM Authorization Risks
Many users believe that participating in well-known or audited projects guarantees the safety of their funds. However, no matter how sophisticated a project is designed, it is not immune to hacking, especially in the decentralized space. If an application or platform you originally trusted is compromised, unlimited authorizations will enable smart contracts to control your wallet's assets without restrictions, increasing risk.
Users often grant authorizations to smart contracts for convenience, only to forget about them later, which increases potential risks. Over time, these forgotten authorizations become hidden vulnerabilities that can be exploited by attackers at any time. Once a project's security is threatened, hackers can bypass you and directly exploit these unlimited authorizations to drain your funds. Failing to limit or regularly revoke authorizations is akin to forgetting to lock your door, exposing your assets to significant risks. Therefore, careful management of authorizations is crucial in the Web3 ecosystem.
You may want to understand how a project's security can be threatened. There are two common methods: exploiting vulnerabilities in smart contract code or manipulating developers through social engineering attacks. Both can open the door for attackers to access user funds without authorization.
Exploiting Smart Contract Vulnerabilities
Smart contracts are the backbone of blockchain, supporting functionalities such as token creation, lending, staking, and bridging. However, any software code may have vulnerabilities. These vulnerabilities are the primary targets for attackers, especially for popular projects with large user bases or significant funds.
Below is an overview of the general process of such attacks.
Finding Suitable Targets: Hackers typically target well-known projects, analyze their smart contracts, and look for exploitable vulnerabilities. Due to the transparency of blockchain, this process requires not only skill but also patience to carefully search for coding errors or logical oversights.
Identifying Vulnerabilities: Once a vulnerability is discovered, attackers can access the project contract without authorization. At this point, their goal becomes clearer: to drain funds. This means emptying liquidity pools and lending reserves or directly exploiting users interacting with the compromised contract.
Loss of Funds: If users grant unlimited authorization to the compromised contract, the risk increases significantly. With such authorizations, the contract can access tokens in the user’s wallet without restrictions. Attackers can execute functions like transferFrom() to withdraw token balances multiple times. As long as the unlimited authorization remains valid, any new deposits in the same wallet are also exposed to risk.
Unless authorizations are revoked, users' existing funds and future deposits may be at risk of being stolen. Unlimited authorizations may seem convenient, but they can quickly become serious vulnerabilities. Therefore, always check and revoke unnecessary or infrequently used smart contract authorizations regularly. Taking the time to reauthorize is much safer than facing the risk of losing funds.
Social Engineering Attacks
Although smart contracts may have vulnerabilities, human error often poses a greater risk. Attackers target developers or project owners, leveraging their trust to gain access to sensitive systems. One common method is malware scams, where criminals trick individuals into downloading malicious programs. Once installed, such programs can steal private keys, access wallets, or manipulate contracts, draining project funds and user balances. Therefore, social engineering attacks pose a severe threat that can affect the entire ecosystem.
Real Case Studies
Vulnerabilities in Smart Contract Upgrades: LI.FI Protocol
There was a vulnerability in the smart contract upgrade of the LI.FI platform that allowed attackers to call any contract without proper verification. By doing so, attackers could extract funds from wallets that granted unlimited token authorization to the LI.FI contract without further user authorization. As vulnerabilities can arise at any time, users must always act cautiously and regularly revoke authorizations to safeguard their funds.
Multiple Signatories Targeted: Radiant Capital
Malicious actors compromised the devices of three multi-signature holders, thereby controlling the multi-signature wallet of Radiant Capital. With this access, they transferred ownership of the wallet to themselves and forcibly updated the lending pool contract. Through this update, they were able to withdraw all funds from the lending pool and user wallets that had granted unlimited authorization. Therefore, users who have not revoked unlimited authorizations remain at risk, especially on specific blockchains.
This case illustrates that failing to revoke authorizations after a project is compromised is a dangerously reckless act. As shown in the image below, this user of the Web3 wallet had granted unlimited authorization to the compromised Radiant Capital lending pool contract. This 'unlimited' permission means the contract can access and withdraw tokens from the user's wallet without restrictions.
As long as the authorization is valid, attackers can repeatedly extract BUSC-USD from the user's wallet. Furthermore, since the contract retains the authorization to withdraw funds, any new funds deposited into the wallet are also at risk. This case advises users to promptly check and revoke related authorizations when a project is compromised to protect their assets.
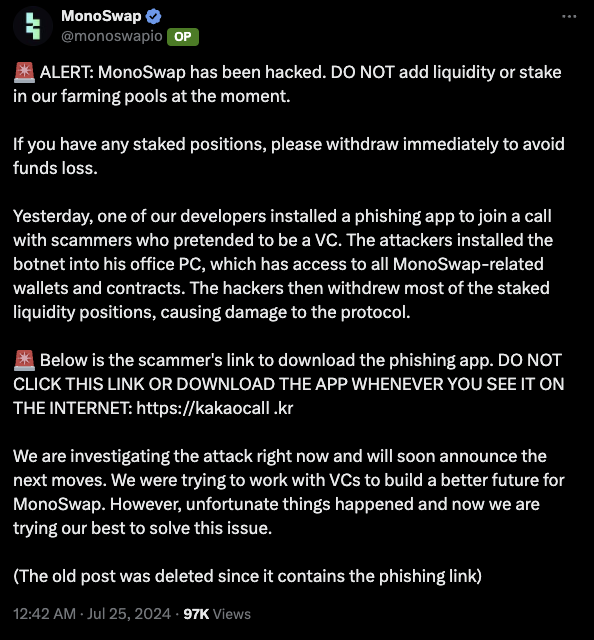
Social Engineering Attack: Monoswap
The attacker impersonated a venture capitalist and conducted a targeted scam against Monoswap developers. They invited the developers to participate in a conference call that allegedly discussed funding opportunities, tricking them into installing a malicious counterfeit version of the Kakaotalk instant messaging application. Unbeknownst to them, the attacker took this opportunity to install a botnet on their office computer, which could access wallets and contracts related to Monoswap through that computer.
Through this access, criminals extracted most of the staked liquidity positions, causing significant losses to the protocol and its users. This incident demonstrates that we should always adopt strict security protocols and authenticate the legitimacy of applications or communication channels before granting access to sensitive systems.
Methods of Self-Protection
In the Web3 world, staying vigilant is key to ensuring asset security. While no system can achieve absolute zero risk, taking proactive measures can significantly reduce potential threats. Below are methods for self-protection:
Cautious Authorization
Avoid granting unlimited token authorizations, even for reputable projects. Limiting authorizations adds an extra layer of security, ensuring that when a project is compromised, attackers cannot exploit that authorization to steal your assets.
Regularly revoke authorizations that are no longer in use
Learn to regularly check and revoke token authorizations from contracts that are no longer in use. A simple step can reduce the risks posed by malicious attacks or accidental vulnerabilities to your assets.
Conduct Due Diligence
Before authorizing contracts, take some time to validate them using reputable security tools like honeypot.is. Although such tools cannot guarantee absolute security, they provide valuable insights into potential risks, which is far better than not verifying at all. By developing these habits, you can build a strong barrier against potential threats with a cautious attitude, allowing you to navigate the Web3 world safely.
Use Binance Web3 Wallet
Use Binance Web3 Wallet and other trusted tools to protect your wallet. This wallet prioritizes user security and is equipped with powerful features to address common Web3 threats, including abuse of authorization.
When a project is compromised, Binance Web3 Wallet quickly takes action to protect users. The system sends immediate security alerts and in-app notifications urging users to revoke risky authorizations or secure their assets. Before completely revoking risky smart contract authorizations, the system continuously reminds users with pop-ups, ensuring they take action to protect their funds.
These proactive protection measures help users stay informed and respond quickly, thereby reducing potential losses.
Stay Informed About New Developments
In the ever-evolving DeFi space, knowledge is the best defense. You can learn about the latest security news, project developments, and emerging vulnerabilities through Binance Academy. For deeper insights into potential threats, please refer to our Scam Awareness Series. These resources provide valuable insights to help you identify scams, protect against new risk threats, and safeguard your ecosystem journey.
Conclusion
In the Web3 world, simply developing a few good habits can significantly enhance asset security. Regularly check your authorizations, use reliable tools like Binance Web3 Wallet, and stay updated through resources like Binance Academy. While these steps may seem small, they can effectively protect your funds and allow you to enjoy the limitless possibilities of decentralized finance with peace of mind.