Key takeaways
Derived from the English verb "to fish", phishing is a type of cyberattack where scammers "go fishing" for sensitive personal information by pretending to be an individual or a reputable company you trust.
The most common phishing tactics include impersonation, using strong or threatening language, and sending dangerous links.
Attackers often change the sender's identity to make it appear that their email comes from a trusted source.
If in doubt about the legitimacy of an email purportedly sent from Binance, contact Binance Customer Support and provide them with the EML file of the email along with relevant screenshots .
Your Binance account could be the target of phishing attempts. Learn how to protect your crypto funds with our comprehensive guide.
The skills needed to break into Binance's security system are beyond the reach of average hackers, but they do have the tools to trick you into revealing your username, password and your two-factor authentication (2FA) code.
Why go through the trouble of breaking into a super-secure safe when you can just persuade its owner to give you the keys? This is the basic principle of phishing: exploiting human errors and emotions.
Keep reading to learn more about phishing, how this scam works, and how to protect your coins from the most common phishing techniques.
What is phishing and how does it work?
Derived from the English verb "to fish", phishing is a common type of cyberattack where scammers "go fishing" for sensitive personal information by pretending to be a well-known individual or company that you trust, for example Binance. The most common phishing tactic is sending emails: these sneaky messages are easy to write and, to some, look very similar to their legitimate counterparts.
It's a method that seems simple, but it works: most cyberattacks start with a phishing email. A study by email security company Valimail found that more than three billion messages impersonating a person or company are sent every day, representing 1%. of the number of emails in circulation.
Knowing how to identify and avoid falling for phishing emails is vital to protecting your cryptos and personal information. Let’s look at some common examples first.
Three Examples of Phishing Emails
The following paragraphs briefly outline the tactics scammers use to send their phishing emails: impersonation, pushy or threatening language, dangerous links... We've also included several real-life examples to help you better understand each technique.
1. Identity theft
Identity theft is a tactic that involves creating fake domain and sender names that resemble official names in order to deceive the recipient. The goal is to trick them into thinking the email is legitimate because part of the sender's address looks trustworthy, such as "binance.com."
Here's a real-life example where scammers used the address "do-not-reply@ses.binance.com", which looks official until you notice the extra "ses" in the sender address before “binance.com”.
2. Urgent or threatening language
Phishing emails often create a sense of urgency, fear, or curiosity in the recipient in order to manipulate their emotions into taking immediate action. For example, it can trick you into believing that an unexpected withdrawal has been made from your account, leading you to "reset" your password when in reality, you are about to reveal it to a scammer.
Here's an example of a phishing email that claims the user made an unexpected withdrawal: Note the tone of the boxed section, which is deliberately written in a way to confuse and scare the recipient with phrases like "block your account » and “protect all your funds”.
3. Dangerous links and fake attachments
Phishing emails usually contain links to fake websites similar to their legitimate counterparts. They may also include attachments like PDFs, executable files, or reworked applications that contain scripts or malware. Opening these attachments can give hackers unauthorized access to your devices, allow them to steal sensitive information or even transfer funds without your consent.
Here is an example of a phishing email containing a malicious link: Clicking [Verify Email] leads to a fake Binance login page that prompts for a username and password . This can then allow scammers to recover Internet users' data to resell them or steal their accounts and funds.
Four ways to unmask a phishing attempt
Now that we've shown you some examples of phishing emails, let's discuss some ways to identify them
1. Binance Verify
Have you received an email from Binance that seems suspicious? First of all, check the sender's address on Binance Verify: if the tool shows you an "Unverified Source", it means that this email is probably dangerous.
Even if the source address is validated by Binance Verify, this may be impersonation: as explained previously, this tactic is commonly employed by scammers to make their communications appear legitimate. They use domain names very similar to their legitimate counterparts or spoofed headers in the "Reply" or "Return Path" fields.
Aside from sender addresses, Binance Verify can also check any social media accounts and website links that the questionable email contains.
Social media accounts
If the email received invites you to contact a “Binance employee” on social media (e.g. Telegram, Facebook or WeChat), consider checking their username on Binance Verify .
The image below shows the screen that appears when the Binance account username is real. Remember that criminals often impersonate company employees: Binance Verify is just one of many ways to verify an individual's identity.
Website Links
Use caution when clicking on website links in emails. To verify a Binance URL, right-click on it and select “Copy link”, then paste it into Binance Verify to verify the authenticity of the website. The image below shows the screen that appears when Binance Verify determines that the website is an official Binance domain.
2. Code anti-phishing
We strongly advise you to configure an anti-phishing code if you have not already done so. This is a simple procedure that only takes a few minutes, and once done, every email sent from Binance will mention the unique combination of numbers and letters you have defined.
This is what an email from Binance looks like with and without the anti-phishing code: Be wary of emails supposedly from Binance that do not contain your anti-phishing code.

3. Checking the EML file
Download the email as an EML file to retrieve additional hidden information for verification. Although more technical, this method is very effective in detecting phishing attempts.
SPF/DMARC/DKIM
For example, you can open the file and perform an SPF/DMARC/DKIM check. If all or some of the checks fail (for example, the check says "dkim=fail"), the email most likely came from an unauthorized source.
IP address reputation
In the EML file, you can also find the IP address and compare it to addresses reported for illegal activities. Simply copy and paste the address into an IP reputation checker like abuseipdb or virustotal. Note: These databases sometimes contain no information if the verified IP address is too recent. Always consult several sources before drawing your own conclusions.
4. Contact Binance customer service
If you have any concerns about an email received, we recommend contacting Binance customer support with screenshots and the EML file. Of all the methods described in this guide, this one is truly foolproof: once you receive your file, our highly experienced phishing team will help you verify the authenticity of the email.
To download the EML file, follow the steps detailed in the paragraph below.
Uploading an EML file
Let's see how to download email contents as EML file from Gmail and Outlook.
Gmail
Open the email you want to download in EML format. Click the three dots in the upper right corner of the email.
From the drop-down menu, select “Download Message.”
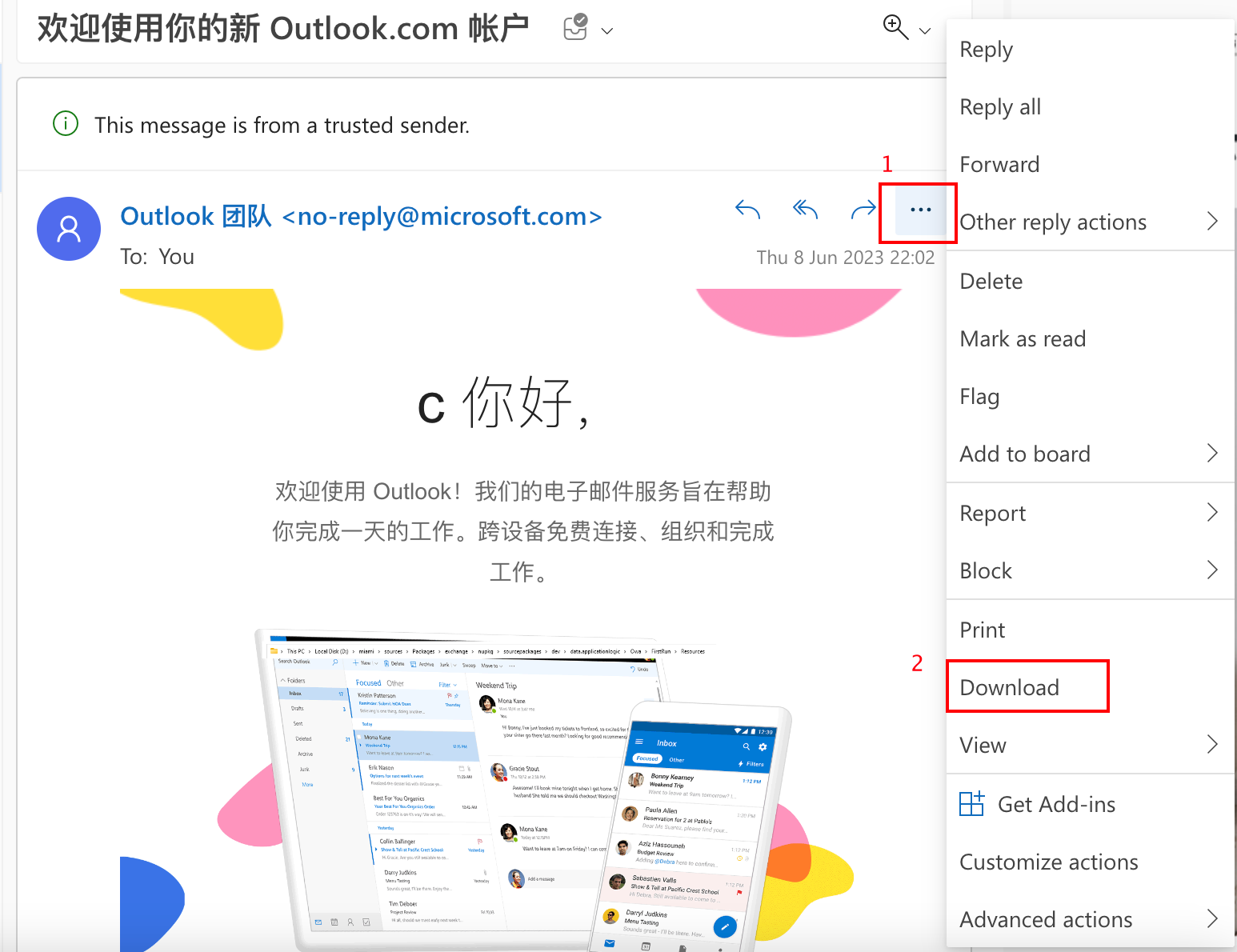
Outlook
Open the email you want to download in EML format. Click the three dots in the upper right corner of the email.
From the drop-down menu, select “Download”.
Once the email is downloaded, right-click the EML file and select [Open with], then [Other]. Then select TextEdit on macOS or Notepad(++) on Windows.
How to escape phishing attempts?
Stay vigilant against phishing attempts and learn how to protect your funds today to avoid future disaster. Here's a quick summary of best practices to adopt:
Configure your anti-phishing code using this guide.
First of all, search for any email address, URL or any username of “Binance” on Binance Verify.
Don't click on questionable links: you could accidentally install malware on your device or access a fake site created to collect your sensitive information.
Do not disclose any personal information to a stranger, including your login information, phone numbers, bank accounts, wallet recovery phrases, or private keys.
Enable two-factor authentication (2FA): If your account information is stolen, 2FA can make it more difficult for a scammer to take over your account.
Only interact with legitimate businesses in the course of business, and be wary of invitations to “free competitions” or “airdrops” received via email.
If you are still in doubt about an email, ask Binance Customer Support for help: we will be happy to check the EML file for you.
For more information
Today's Catch: Anti-Phishing Codes and How to Protect Yourself
Stay safe: What to do if your account has been compromised?
How to protect your cryptos from SMS spoofing attacks?
Trade anywhere with the Binance mobile crypto trading app (iOS/Android)
Find us on :
Instagram : https://www.instagram.com/binancefrench
Twitter : https://twitter.com/LeBinanceFR
Facebook : https://www.facebook.com/BinanceFrance
Telegram : https://t.me/BinanceFrench
Risk Warning: Digital asset prices are subject to high market risk and price volatility. The value of your investment may fall as well as rise, and you may not get back the amount invested. You are solely responsible for your investment decisions and Binance is not responsible for any losses you may incur. Past performance is not a reliable indicator of future performance. You should only invest in products that you are familiar with and whose risks you understand. You should carefully consider your investment experience, financial situation, investment objectives and risk tolerance and consult an independent financial advisor before making any investment. This does not constitute investment advice, nor an inducement or recommendation to trade in any digital asset. For more information, see our Terms of Use and Risk Warning.