Contents
Introduction
What is a private key?
What is a hardware wallet?
Why use a hardware wallet?
Limitations of hardware wallets
Hardware Wallet Review 2020
Ledger Nano S
Ledger Nano X
Trezor One
Model T safe
Cobo Vault
CoolWallet S
SafePal S1
KeepKey
To conclude
Introduction
When it comes to cryptocurrencies, quality storage is of utmost importance. The world of cryptocurrencies is dangerous: bad actors are everywhere and have an abundance of strategies to steal user funds. Having a strategy in place to protect your cryptos should be your top priority.
You have a range of storage options, each with its own security and usability trade-offs. Most often, newcomers will stick to exchanges. These platforms provide many with their first exposure to cryptocurrencies and allow users to store their funds in an online wallet. But the user is not technically in control of their funds. If the exchange is hacked or taken offline, it may not be able to recover its funds.
Users may not need to withdraw their cryptocurrency from the exchange. They may not have the skills to do so, or even view childcare solutions as safer. After all, self-custody can lead to the loss of funds if the user makes a mistake.
Thinking about taking control of your cryptocurrency yourself can be intimidating. But from a security point of view, hardware wallets remain the first choice. In this article, we'll explain what they are, how they work, and why you should use one.
What is a private key?
Your private key is your passport to the cryptocurrency ecosystem. In many ways, it's like a real key. With this information, you can unlock your funds for spending. If someone else has access, they can steal your cryptocurrency. If you lose the key, you lose access to your funds. There is no forgotten password button in a decentralized environment. There is also no bank you can call to reverse fraudulent transactions.
To summarize, private keys should be kept secret and secure. They are extremely valuable for cryptocurrency users. Unsurprisingly, hackers and scammers are constantly trying to steal them, using phishing techniques or malware.
Storing your keys is simple: they're just strings of numbers and letters. They can be written down on paper and stored securely. However, in order to use the keys to transfer money, they must be on a device that creates proof that you can spend your funds.
What is a hardware wallet?
Hardware wallets are devices specially designed to store private keys securely. They are considered more secure than desktop or smartphone software wallets, mainly because they do not connect to the Internet at any time. These properties significantly reduce the attack vectors available to malicious actors because they cannot manipulate the device remotely.
A good hardware wallet ensures that private keys never leave the device. They are normally kept in a special place on the device which does not allow them to be modified or deleted.
As hardware wallets remain offline, they must be used with another device. Because of the way they are designed, they can be plugged into infected PCs or smartphones without any risk of private key leaks. From there, they interact with software that allows the user to view their balance or make a transaction.
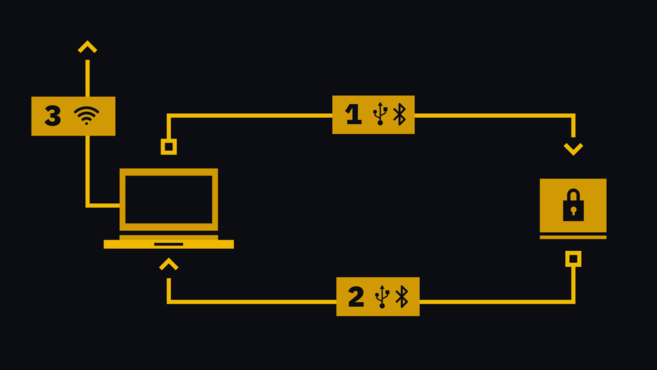
Once the user creates a transaction, they send it to the hardware wallet (1 in the diagram below). Note that the transaction is still incomplete: it must be signed by the device's private key. Users confirm that the amount and address are correct when prompted on the hardware device. At this point, it is signed and sent back to the software (2), which broadcasts it to the cryptocurrency network (3).
Why use a hardware wallet?
Wallets that store private keys on Internet-connected computers or smartphones make user funds vulnerable to a wide range of attacks. Malware can detect cryptocurrency activity on these devices and steal user funds.
A hardware wallet is like an impenetrable safe with a small opening. When the user wants to create a transaction that the network will accept, they pass it through the opening. Imagine that, on the other side of the opening, an elf is doing the cryptographic magic that signs the transaction. The elf will never leave the chest. There is no door, and he cannot fit through the opening. All it can do is receive transactions and resend them.
Even if someone manages to take over your hardware wallet, you have additional protection in the form of a PIN. Devices are often reset if the incorrect combination is entered a certain number of times.
Funds that are not actively used, those that are not spent, staked, loaned or traded, should be stored in an offline storage solution. A hardware wallet offers a convenient way to achieve this for users, even those with limited technical knowledge.
Hardware wallets should be backed up in case of loss, theft or destruction. During initialization, the user will often be prompted to save their seed phrase, a list of words that can be used to recover their funds on a new device. This phrase gives anyone the ability to spend the funds, and should be treated like any item of value. Users are recommended to write them down on paper (or engrave them on metal) and keep them in a safe place.
Limitations of hardware wallets
Hardware wallets, like other forms of storage, also suffer from compromises. Although they are one of the safest ways to hold cryptocurrencies, they still have some limitations. They aim to strike a balance between security and usability. Software and smartphone wallets are convenient, while hardware wallets can be cumbersome to use (since two devices must be used to send funds).
Additionally, hardware wallets are not completely foolproof. A physical threat to a user can prompt them to unlock a wallet for the attacker, but there are other vectors as well. Competent threat actors can hack the device if they gain physical access.
To date, however, no hack has been able to access a hardware device's private keys in a realistic scenario. When vulnerabilities are reported, manufacturers are usually quick to patch them. This does not mean that these attacks are impossible. The researchers were able to demonstrate the feasibility of attacks against the most popular wallets.
Supply chain attacks can also be effective in compromising the security of a hardware wallet. This happens when the threat actor intercepts a wallet before it is delivered to the user. From there, they can tamper with its security and steal funds once the user has stored funds there.
Another limitation is that hardware wallets involve taking custody of your wallet. Many consider this to be an advantage because there is no third party responsible for managing your funds. But it also means that if something goes wrong, there is no recourse.
Hardware Wallet Review 2020
At Binance Academy, we have been working on a series of reviews of the most popular hardware wallets on the market.
Ledger Nano S
Arguably one of the most popular hardware wallets to date, the Ledger Nano S is considered a must-have by both long-term holders and high-frequency traders. Read our full review of the Ledger Nano S 2020.
Ledger Nano X
The successor to the Ledger Nano S, the Nano X features an impressive number of upgrades, including wireless functionality and support for more cryptocurrencies. Read our full review of the Ledger Nano X 2020.
Trezor One
A product that revolutionized the hardware wallet industry and still competitive, affordable but high performance, the Trezor One remains the gold standard for many cryptocurrency holders. Read our full review of the Trezor One 2020.
Model T safe
The supercharged Trezor One. Although it's priced higher, you'll benefit from a touchscreen, support for multiple currencies, and SD card compatibility for future updates. Read our full review of the 2020 Trezor Model T.
Cobo Vault
The portfolio of those preparing for the apocalypse. A non-networked, touchscreen device protected by a sturdy metal casing. For those who take security seriously. Read our full review of the Cobo Vault 2020.
CoolWallet S
With the dimensions of a credit card, the CoolWallet S is certainly an unforgettable device. Although it makes sacrifices on UI/UX, it will appeal to those looking for something different. Read our full review of the CoolWallet S 2020.
SafePal S1
For its price, SafePal implements some very nice security features, while keeping its interactions with other devices to a minimum. Read our full review of the SafePal S1 2020.
KeepKey
A sleek device with native ShapeShift integration. However, it is necessary to register to make the most of its potential. Read our full review of the KeepKey 2020.
Did we forget your favorite device? Let us know by tweeting us at @BinanceAcademy!
To conclude
Hardware wallets still have more advantages than limitations. When it comes to storage solutions, it's impossible to compete with the level of security that hardware wallets offer. There is simply no substitute for offline storage, which eliminates much of the risk associated with self-custody of funds.
When looking for a hardware wallet, users should educate themselves about the different options available to them. There are a number of devices on the market, each with their own features, different supported cryptocurrencies, and varying user experiences.








