Web3 Security: The Danger of Unlimited Approvals on Ethereum Virtual Machine Chains
Main Takeaways
In the world of Web3, granting unlimited approvals creates vulnerabilities that hackers can exploit through smart contract flaws or social engineering.
Regularly review and revoke unnecessary approvals to prevent unauthorized access to your assets.
Safeguard your funds with tools like Binance Web3 Wallet and constantly stay informed about Web3 security risks.
In a world of decentralized finance, what’s the cost of one overlooked approval? While smart contracts can simplify transactions, these interactions also introduce unique security risks, particularly when users grant unlimited permission to third parties to access and manage their funds. In our previous blog, we covered the risks of approvals to smart contracts and externally owned accounts (EOAs). In this article, we’ll dive deeper into additional approval risks specifically on Ethereum Virtual Machine (EVM) chains and how you can safeguard your assets from these threats.
Understanding Approval Risks on EVM
Many users assume that interacting with well-known or audited projects guarantees that their funds are completely safe. However, even the most meticulously designed projects, especially in the decentralized space, are not immune to hacks. Unlimited approvals heighten the risk by giving smart contracts unrestricted control over your wallet’s assets when the application or platform you had trusted in the past gets compromised.
This becomes even more dangerous because users often approve smart contracts for convenience and subsequently forget about them. Over time, these forgotten approvals turn into hidden vulnerabilities, ready to be exploited. If a project’s security is compromised, hackers can use these unlimited approvals to drain your funds instantly, without needing any further action from you. Failing to limit or periodically revoke approvals is like leaving your door unlocked, making your assets an easy target. This is why managing your approvals carefully is essential in the Web3 ecosystem.
You may wonder how a project’s security could be compromised. Two common methods stand out: exploiting vulnerabilities in smart contract code and using social engineering tactics to manipulate developers. Both approaches can open the door for attackers to gain unauthorized access to user funds.
Exploiting Smart Contract Vulnerability
Smart contracts form the backbone of blockchain functionality, enabling features like token creation, lending, staking, and bridging. However, as with any software, no code is entirely free from vulnerabilities. These weaknesses become prime targets for attackers, especially in popular projects with large user bases or substantial funds at stake.
Here’s how such an attack can unfold.
Finding a Suitable Target: Hackers zero in on well-known projects, analyzing their smart contracts for exploitable flaws. With blockchain’s transparent nature, this process is as much about patience as it is about skill, as attackers meticulously search for coding errors or logic oversights.
The Breach: Once a vulnerability is identified, attackers gain unauthorized access to the project’s contracts. From here, their objective is clear: siphon funds. They aim to drain liquidity pools, lending reserves, or directly exploit users who interact with the compromised contract.
The Drain: The risk is amplified significantly for users who have granted unlimited approvals to the compromised contract. These approvals provide unrestricted access to the tokens in their wallets. Attackers can execute functions like transferFrom() to withdraw the entire token balance, not just once, but repeatedly. Any new deposits into the same wallet also remain vulnerable as long as the unlimited approval is active.
As a result, users risk losing both their current funds and any future deposits until the approval is revoked. While unlimited approvals may seem convenient, they can quickly become a serious vulnerability. That's why it's important to develop the habit of reviewing and revoking unnecessary or rarely used smart contracts. It's always safer to take a minute to re-approve a contract than risk losing your funds.
Social Engineering
While smart contracts can be vulnerable, human error is often the key to a breach. Attackers target developers or project owners, exploiting trust to gain access to sensitive systems. A common tactic is malware scams, where bad actors trick individuals into downloading malicious programs. Once installed, these programs can steal private keys, access wallets, or manipulate contracts, draining both project funds and user balances. Hence, social engineering is a serious threat that can impact the entire ecosystem.
Real-Life Examples
Vulnerabilities in Smart Contract Upgrades: LI.FI Protocol
A vulnerability during a smart contract upgrade on the LI.FI platform allowed an attacker to execute arbitrary calls to any contract without proper validation. This flaw enabled the attacker to exploit wallets that had granted infinite token approvals to LI.FI contracts. By leveraging these unchecked permissions, the attacker could withdraw funds from these wallets without requiring any further authorization from the users. Since vulnerabilities can surface unexpectedly, it's always safer to err on the side of caution by revoking permissions whenever possible.
Compromising Multi-sig Signers: Radiant Capital
Malicious actors targeted and compromised the devices of three multi-sig signers, gaining control of a multi-signature wallet belonging to Radiant Capital. Using this access, they transferred ownership of the wallet to themselves and pushed an update to the lending pool contracts. This update allowed them to drain all funds from the lending pools, as well as from user wallets that had granted unlimited approvals. Users who haven’t revoked their unlimited approvals remain at risk, particularly on certain blockchains.
This case illustrates the dangers of not revoking approvals following a breach. One Web3 wallet user as shown below had granted unlimited approval to the compromised Radiant Capital Lending Pool contract. The "unlimited" allowance meant that the contract could withdraw tokens from the user’s wallet without restriction.
As long as the approval remains active, the attacker can repeatedly drain BUSC-USD from the user’s wallet. Furthermore, any new deposits into the wallet are also at risk, as the contract retains authorization to withdraw funds. This scenario emphasizes the critical need for users to review and revoke approvals when a security breach occurs to safeguard their assets.
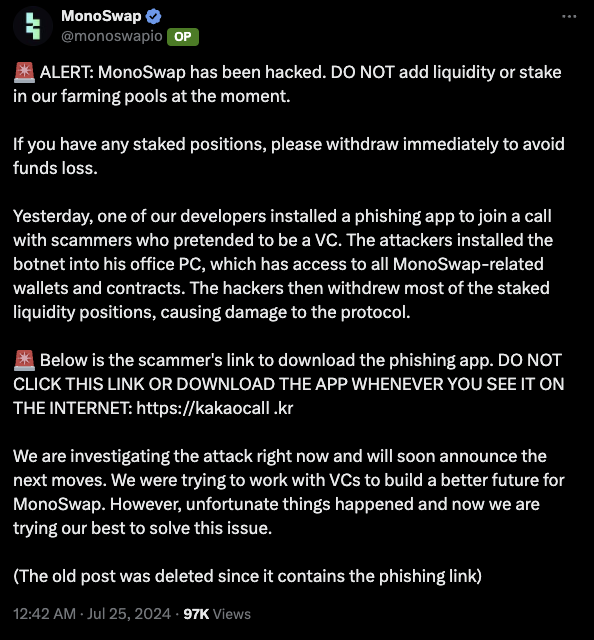
Social Engineering: Monoswap
A Monoswap developer fell victim to a targeted scam when attackers posed as venture capitalists. To join a call where they would purportedly discuss a funding opportunity, the developer was tricked into installing a malicious imitation of the Kakaotalk messenger. Unbeknownst to him, the attackers used this opportunity to install a botnet on his office PC, which had access to Monoswap-related wallets and contracts.
With this access, the bad actors withdrew the majority of staked liquidity positions, inflicting significant damage on the protocol and causing losses for its users. This incident underscores the importance of maintaining strict security protocols and verifying the legitimacy of any application or communication before granting access to sensitive systems.
Ways to Protect Yourself
In the world of Web3, staying vigilant is key to keeping your assets secure. While no system is entirely risk-free, taking proactive steps can significantly reduce your exposure to potential threats. Here’s how you can protect yourself:
Be Cautious with Approvals
Whenever possible, avoid granting unlimited token approvals, even to reputable projects. Limiting approvals adds an extra layer of security, ensuring attackers cannot exploit them if a project is compromised.
Habitually Revoke Unused Approvals
Make it a habit to regularly review and revoke token approvals for contracts you no longer use. This simple practice reduces the chances of your assets being exposed to malicious exploits or unforeseen vulnerabilities.
Conduct Due Diligence
Before approving a contract, take a moment to verify it using reputable security tools such as honeypot.is. While these tools cannot guarantee absolute safety, they provide valuable insights into potential risks and are far better than skipping the check altogether. By adopting these habits, you take control of your safety in Web3, turning caution into your strongest safeguard against potential threats.
Use Binance Web3 Wallet
Protect your wallets with trusted tools like Binance Web3 Wallet, which prioritizes user safety with robust features to counter common Web3 threats, including approval abuse.
When a project is compromised, Binance Web3 Wallet acts swiftly to safeguard its users. Security alerts and in-app notifications are immediately sent, urging users to revoke risky approvals or secure their assets. A persistent pop-up remains visible until the risky smart contract approval(s) are fully revoked, ensuring users take action to protect their funds.
These proactive measures keep users informed and allow them to respond quickly, reducing the risk of potential losses.
Stay Informed and Updated
Knowledge is your best defense in the ever-evolving DeFi landscape. Stay up-to-date with security news, project developments, and emerging vulnerabilities with Binance Academy. For a deeper dive into potential threats, check out our Know Your Scam series. These resources provide valuable insights into recognizing scams and protecting yourself from the latest risks in the ecosystem.
Final Thoughts
In the world of Web3, a few simple habits can make all the difference in keeping your assets safe. Regularly check your approvals, use reliable tools like Binance Web3 Wallet, and stay informed through resources like Binance Academy. With these small but important steps, you can keep your funds secure and focus on enjoying the possibilities decentralized finance offers.