X Account Compromises in Crypto: From Individual to Industry Implications
Main Takeaways
As a communication channel between projects and communities, X plays a key role in the crypto space. However, the platform can also be vulnerable to malicious actors, as seen in various cases this year.
Scammers use a variety of methods to gain control of X accounts, including phishing attacks, SIM swap attacks, and brute-force attacks. It’s important to stay vigilant and avoid suspicious messages, emails, websites, or links.
Keep your X account secure by using strong passwords, updating them regularly, activating 2FA, managing access to your account, and staying updated on common hacking techniques.
X and the Cryptocurrency Industry
Earlier this year, on January 9, the official X account of the US Securities and Exchange Commission (SEC) was compromised through a SIM swap attack. Subsequently, the attackers announced the false approval of spot bitcoin exchange-traded funds (ETFs) a day early, causing unexpected market volatility. Shortly after, the SEC regained control of the account.
X (formerly known as Twitter) plays a key role in the cryptocurrency industry as a communication channel between communities and projects. Through X, the industry is kept updated on essential news from crypto projects and communities. However, given this prominence, account takeover attacks on the platform can pose substantial threats. Today, we will explore the implications of compromised X accounts and tips to keep your online information secure.
What Is a Compromised X Account?
A compromised X account refers to a legitimate, often verified, account falling victim to a malicious actor or group of actors. Their reasons may differ, but the end goal is usually the same: obtaining sensitive information. When a hacker gains control of an X account, they can impersonate the original account holder. In the crypto X community, this can lead to misinformation, financial manipulation, or phishing attacks. Interacting with such accounts poses substantial risks not only to the X account holder but also to the wider crypto community.
There are three main risks associated with compromised X accounts:
Potential distribution of harmful links or malware. This could occur if the hacker uses the hijacked account to send or post dangerous links that, when clicked, could infect a user’s device with malware. Not only does this put the user’s data at risk, but such malware can also give the hacker access to the user’s crypto wallets, therefore putting their assets at risk as well.
Manipulation of followers into making detrimental financial decisions based on misinformation or misleading guidance. This often has implications for the wider crypto community, as investors may lose trust in the ecosystem due to such malicious actions. The repercussions might also cause market swings and disrupt the fair price discovery process.
Security breaches, which reflect negatively on the organization behind the account, damaging their reputation and casting doubt on their competence in protecting user information and funds.
Several notable X accounts have been compromised in 2024 so far, including the SEC, CoinGecko, and Mandiant.
Identifying Compromised X Accounts
Recognizing the signs of a compromised X account is crucial to minimizing potential damage. Let’s explore some common warning signs to watch out for both community members looking in and the owners of the compromised accounts themselves.
Community perspective
If you are an X user reading the posts of another member of the community, look out for the following signs to help assess whether an account has been compromised:
Compromised accounts may start posting unexpected content, diverging from their usual timeline and format. Additionally, these posts can contain common scamming techniques, such as the following:
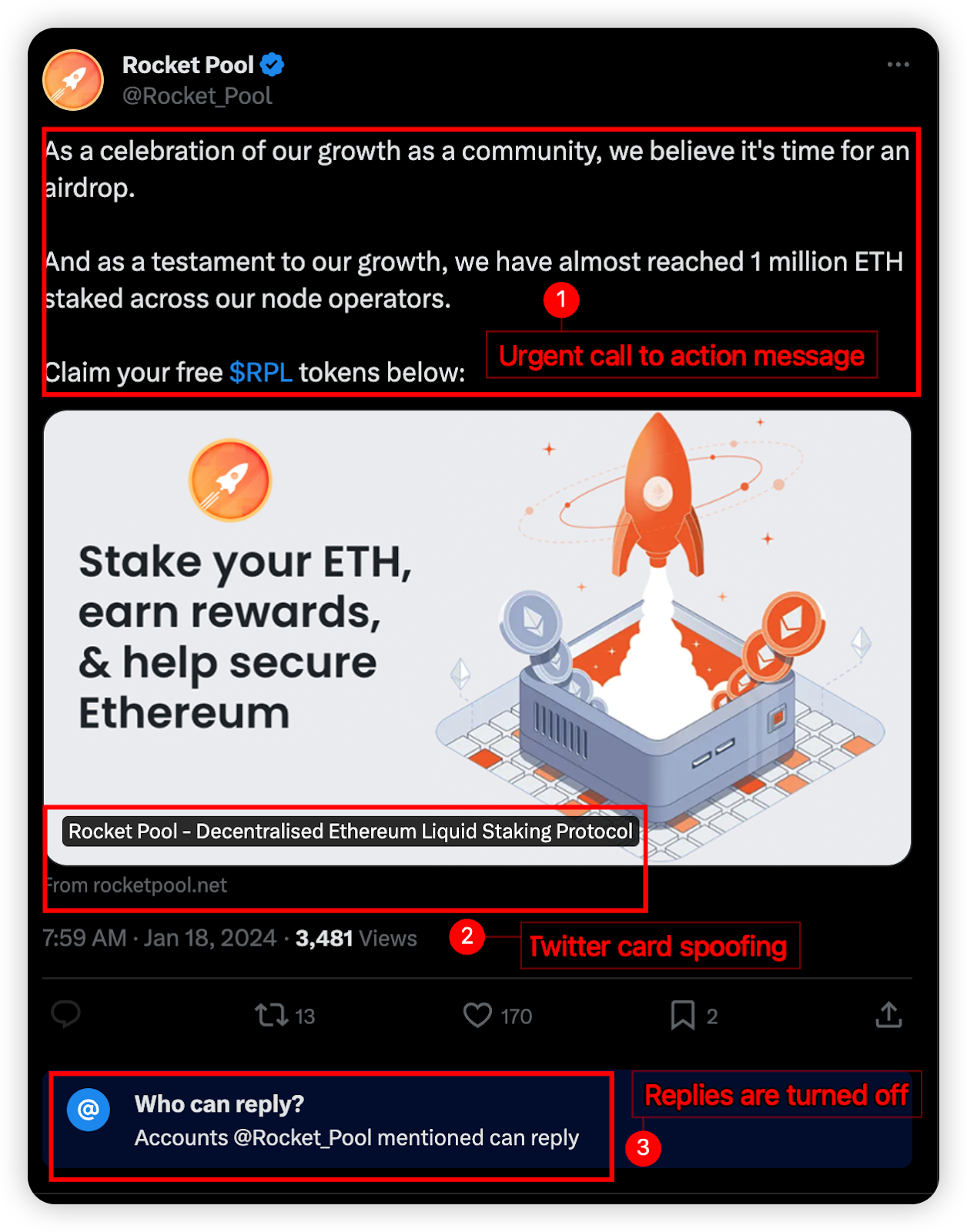
Urgent calls to action, prompting a FOMO effect on the user.
X card spoofing – a technique used by scammers to trick users into clicking malicious links.
Restricted comments or replies, usually to prevent users from calling them out and warning others.
Compromised accounts may start sending unexpected DMs to regular users, aiming to foster trust.
Compromised accounts may block security-related accounts that call them out to prevent people from blowing their cover.
An example of a post by a compromised X account
Account holder perspective
If you are an X user who suspects they may have fallen victim to an account takeover attack, watch out for the following signs to help assess whether your account has been compromised:
Unexpected posts, reposts, or likes appear on your profile.
You are receiving responses to direct messages you did not send.
There are unexpected changes to your account settings, such as login credentials or linked contact details.
Alerts for login attempts or successful logins from unfamiliar locations.
Involuntarily following new accounts.
Messages from your followers about suspicious activity or spam from your account.
Common Techniques and Vulnerabilities
Understanding how hackers compromise X accounts is key to enhancing account security. Learning resources such as this blog and other educational articles can help users stay updated on the latest scam methods. Let’s explore some common fraud techniques and vulnerabilities to look out for.
Phishing: One of the most common scamming techniques is phishing, a type of social engineering attack. When scammers target you, their first goal is often to gain your trust. After successfully doing so, they will ask you to click and authorize X permissions through a third party. This third-party site then gains access to your account, allowing them to post or change passwords on your behalf.
SIM swap attacks: These occur when scammers trick phone carriers into sending your texts and calls to a SIM card they control rather than your original one. SIM swapping presents a real threat to X users who’ve linked their accounts with their mobile numbers. Ultimately, scammers leverage this control to gain access to your account.
Password vulnerability and lack of 2FA: Neglecting the security of your account lays the foundation for malicious attacks. Using weak passwords that can fall to brute-force attacks and the absence of two-factor authentication (2FA) turns your account into low-hanging fruit for hackers.
Consequences of Data Breaches: Accounts using the same password across multiple platforms are always at a higher risk of attack. The compromise of one account can easily trigger a domino effect, affecting other accounts as well, be it your X or Binance account.
Malware Attacks: If you’re storing unencrypted passwords on your local desktop and visiting suspicious websites, you’re inadvertently setting the stage for hackers to access your passwords. You are especially vulnerable if you download applications from these suspicious websites.
How to Keep Your Accounts Safe
Understanding the necessary steps to secure your X account is essential to maintaining online privacy and safety. The first and most important step to ensuring the security of your X account is creating a strong password. A strong password should check the following boxes:
Be at least 12 characters long.
Contain varied elements, including a combination of uppercase letters, lowercase letters, numbers, and symbols.
Exclude easily guessable data such as your name, birthdates, or common words.
Be stored in a reliable password manager.
To help ensure the robust security of your X account further, consider adopting the following measures:
Switch to non-SMS-based 2FA, such as authenticator apps or, for maximum security, a hardware authentication device, such as a Yubikey.
Regularly check third-party app permissions and screen for any suspicious approvals. Here is a general guide on how to check these permissions on the X platform: More ⇒ Settings and support ⇒ Settings and privacy ⇒ Security and account access ⇒ Apps and sessions ⇒ Connected apps ⇒ Remove (if suspicious).
Managing third-party app permissions on X
(Note: while these screenshots were taken from the X desktop browser, the general guide above applies to most operating systems)
Be cautious of suspicious communications, and do not interact with any suspicious emails, direct messages, or links from unfamiliar sources.
Use secure and updated devices and networks when accessing your X or Binance accounts.
Stay on top of who has access to your accounts to prevent unauthorized access.
Keep yourself updated on common hacking techniques so you can recognize a threat when you see one.
Companies should continuously review their data privacy and security models to ensure all employees understand their data handling policies. This is especially true when organizational changes occur, such as access being updated as employees leave or enter.
What to Do if Your X Account Is Breached
If your account gets compromised, it is important to react quickly to help mitigate any negative consequences to you or the community.
Reset your X account password and the passwords of all associated accounts.
Cease third-party permissions to prevent further unauthorized access.
Inform your community through an alternative communication channel. Some examples could be Discord or Telegram.
Contact X’s customer support team and inform them of the situation. They will help further in resolving the issue.
Stay Vigilant
At Binance, one of our main goals is ensuring the safety of crypto users. A key part of this initiative lies in educating our users on the latest scam methods and security measures. In an era of escalating cyber threats, ensuring the safety of your digital accounts has become more important than ever before. Particularly in the crypto space, compromised accounts could have large implications for the broader ecosystem.
Understanding common signs of account compromise, being aware of prevalent hacking methods, creating robust passwords, and consistently updating security settings are essential. Each community member must take full accountability for the consequences that follow after their accounts get compromised. As such, keeping X accounts secure must be a high priority. Always remember that the strength of your online security is only as robust as its weakest link.