How Safe is Your Crypto? A Special Peek into Binance's 24/7 Security Protocols

Today’s crypto landscape has changed considerably since the early years. Thousands of new projects have entered the market. We’ve evolved from a niche, tech-heavy community to a diverse ecosystem with mainstream interest. Of course, the road has been bumpy and marred with challenges.
The crypto industry is now at a critical stage. The market will continue to evolve and attract more attention, including unwanted. Web3 companies must prioritize giving their users the crypto experience they deserve: secure, reliable, and transparent.
Users should feel safe from digital threats. They need platforms that are stable, with features that work. They should know exactly what platforms are doing with their money and personal information.
Since the beginning, Binance has always taken the responsibility to prioritize user safety over profit. We launched Binance in 2017 with a simple goal: bring crypto to as many people as possible. Our approach: give the users what they want and always act in their best interest.
We’d like to take this opportunity to share how we secure user assets at Binance, including the many tools available to our users and the security protocols installed in our backend. We implore other Web3 companies to follow the same standards, if you haven’t already done so.
How We Protect You Behind the Scenes
We take a 360-degree approach to user security that covers all bases, including advanced know-your-customer (KYC) protocols, machine-learning risk detection algorithms, and internal staff training against potential security breaches.
Let’s dive into the first and probably the most important measure for any financial institution: KYC and anti-money laundering (AML) protocols.
1. Know Your Customer (KYC) & Anti-Money Laundering (AML) protocols
Binance works with vendors across the globe to create KYC procedures that are compliant in multiple jurisdictions. For example, certain regions may require proof of address or other additional checks.
Our standard KYC process goes above and beyond what financial institutions typically offer. All new users must pass a series of checkpoints — including document and face verification — before they can access any crypto service on our platform.
In addition to KYC, we’ve implemented robust anti-money laundering (AML) processes via internal services and external vendors, like Chainalysis, that support targeted investigations and fund recovery efforts.
2. Multi-factor authentication (MFA)
Multi-factor authentication (MFA) is essential in offering a secure yet user-friendly experience on Binance. We’ve underpinned certain account activities with suitable MFA requirements according to the level of risk.
For example, low-risk activities, such as logging in to check your balance, don’t usually require MFA. However, high-risk activities — especially withdrawals — will always trigger extra verification steps.
3. Real-time monitoring
We use advanced artificial intelligence and machine learning algorithms to detect suspicious activity going in and out of the platform in real time. This includes but is not limited to abnormal logins or transaction patterns.
Our system can send real-time notifications to warn users of potential risks before they click continue. It can also intercept outgoing transactions to known “suspicious addresses” before temporarily restricting user withdrawals.
4. Dark web surveillance
We’re continuously monitoring dark web forums and markets for the latest attack methods, potential threats, and third-party data breaches. All information we collect is proactively shared with law enforcement agencies. Any potential user data we find on the dark web is relayed back to the affected users, with their accounts suspended accordingly.
5. Staff training
Hackers often try to breach companies from the inside through their staff. Some of the biggest brands in the world have suffered massive data breaches just from one employee clicking a simple phishing link.
Staff training is an integral part of Binance's commitment to security. Our team members receive routine education addressing the latest scams and social engineering attacks. We also conduct phishing email drills to ensure our teams are following best practices.
What Tools Can You Use to Protect Your Funds
While we expend significant resources to protect users from the backend, the best defense is ultimately you. Think of your account as a vault inside our platform. We essentially employ an army of soldiers to protect your vault. All of these measures, however, can easily be undermined if you willingly give your vault password or money to a burglar on the outside.
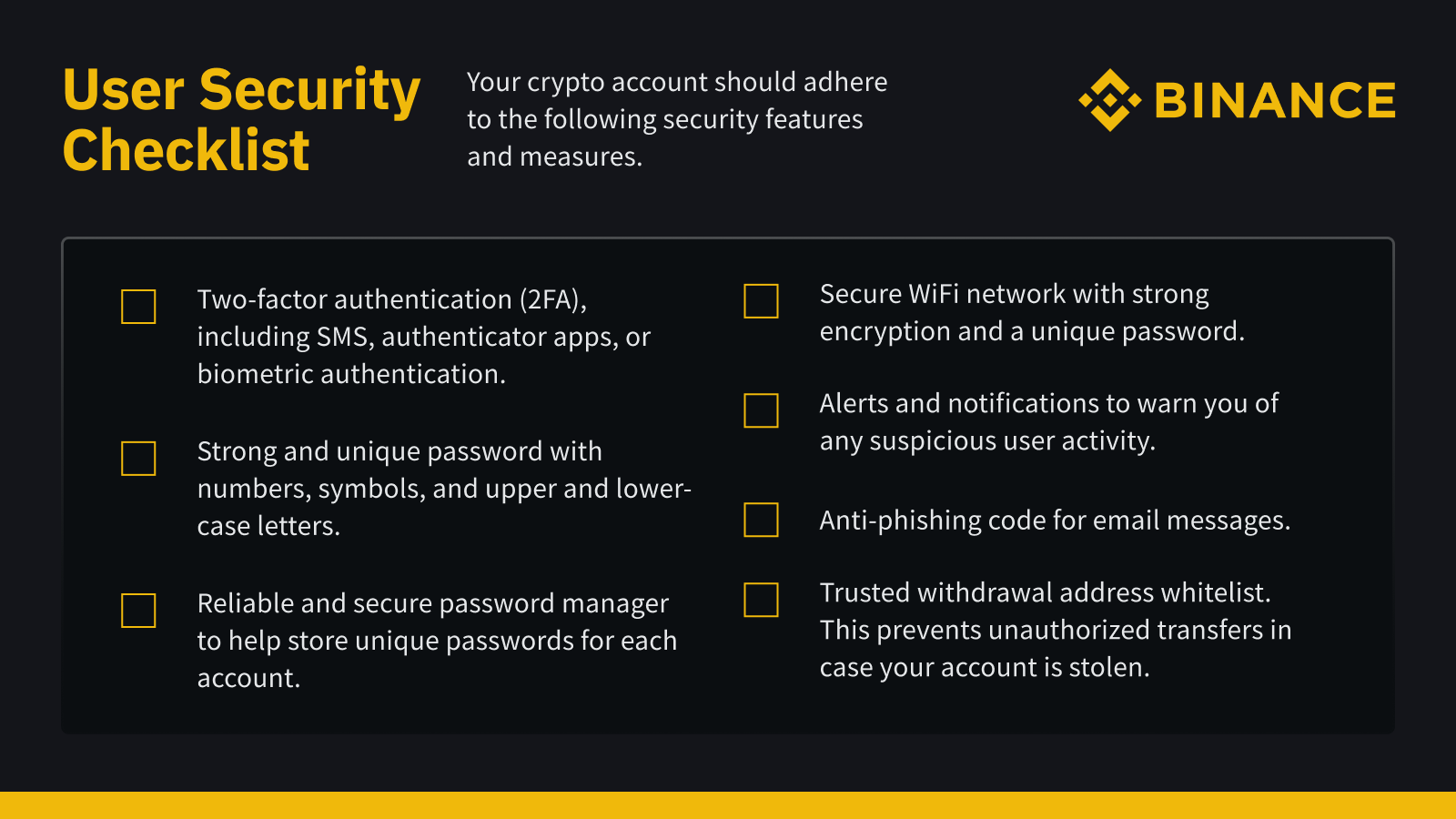
Every Binance user has access to advanced security tools designed to thwart a wide range of threats, from phishing attacks to account takeovers. Notable tools include anti-phishing codes, withdrawal whitelists, and various forms of two-factor authentication.
1. Two-factor authentication (2FA)
Enable two-factor authentication (2FA) on all your platforms, not just Binance. Just using a password simply won’t cut it.
2FA is one of your strongest lines of defense against a hacker. As mentioned previously, your account is a vault in our platform. With 2FA enabled, hackers can’t just walk in even if they have the password to your vault. They’ll face an additional hurdle, an extra step of verification. This can be via your phone, email, or a third-party app.
For more information on setting up 2FA, please refer to our library of FAQ guides. Note that SMS is vulnerable to tactics like SMS spoofing. Binance users have access to a broad selection of 2FA alternatives like Passkey and our very own Binance Authenticator.
2. Anti-phishing code
Once set up, the anti-phishing code feature enables you to identify genuine Binance emails through a unique code only you know. Any email from “Binance” without your anti-phishing code is a scammer.
3. Binance Verify
Binance Verify is an official database anyone can use to verify the authenticity of Binance-related domains, email addresses, phone numbers, WeChat IDs, Twitter accounts, and Telegram IDs.
4. Withdrawal whitelist
You can create a withdrawal whitelist to add trusted withdrawal addresses for specific cryptocurrencies. This can help prevent unauthorized transfers in the event your account is stolen.
5. Alerts and notifications
You can set custom alerts and notifications to stay informed on your account activity. This includes real-time updates regarding new devices, login attempts, and suspicious transactions.
Final Thoughts
By following the security guidelines outlined in this article and making use of the various features offered by Binance, users can fully enjoy the benefits offered by crypto.
The blockchain industry must continue to prioritize security and adhere to high standards. We must instill confidence in not only our own users but also those on the outside. Trust is the foundation of any financial system.
At Binance, we focus on maintaining the highest security standards because it’s the future to a thriving crypto economy. We hope our peers hold the same belief.